S2T Analytics provides Big Data and AI Solutions.

S2T has been providing security agencies worldwide with information crucial for the efforts of law enforcement. Today’s advanced technology is sadly used by criminal factors for various purposes: trade in drugs, human trafficking, forgery etc. This ongoing trend only seems to grow due to the anonymity provided by the dark net. S2T technological solutions provide with an intuitive and efficient platform for data harvesting and analysis. We believe that concrete and useful information is commonly found on the Internet. The abundance of information calls for constant monitoring and analysis - a combination which S2T’s technologies excel in.
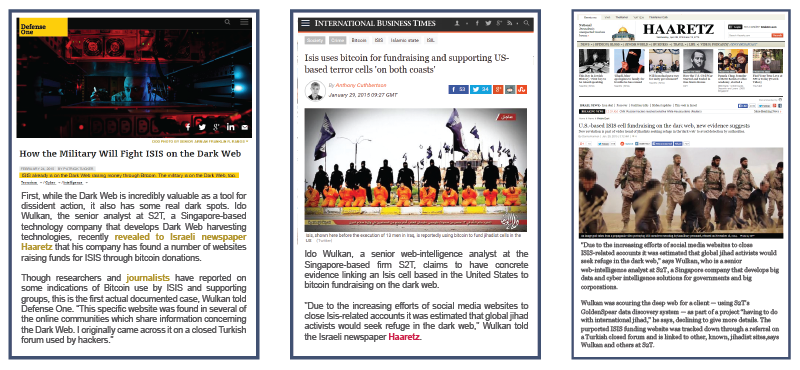
Keep track of the dynamic and ever-developing environment of global-terrorism. On January 2015, S2T’s intelligence team exposed a darknet website hosted on TOR, which raised funds for an American Islamic terror-cell identified with ISIS. The extremist Islamic organization is known for its use of online media for distribution of propaganda and recruitment of new members. Given the recent crackdown on sites, social media profiles and forums used by ISIS, we expect the organisation’s activity to expand to the darknet.
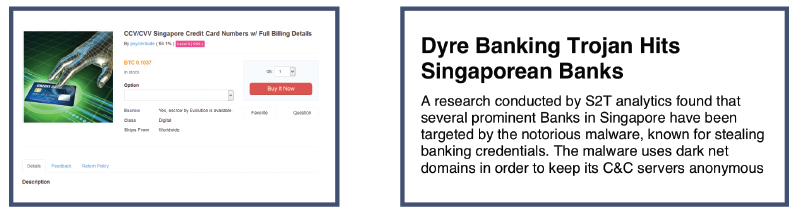
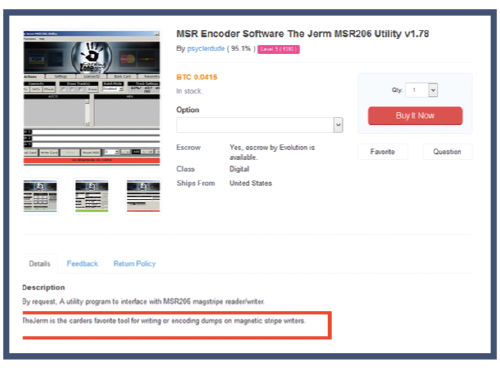
Naturally, the majority of cyber-criminal activity is conducted online. Hackers discuss methods, trends and campaigns on the social-media as well as dedicated online communities. Serving several prominent clients worldwide in the financial sector, S2T has a longtime experience in monitoring the cyber-crime arena and pointing out crucial developments in that field. We believe that an active approach towards cyber-security is required in order to better defend against the ever-developing threats which this arena poses: