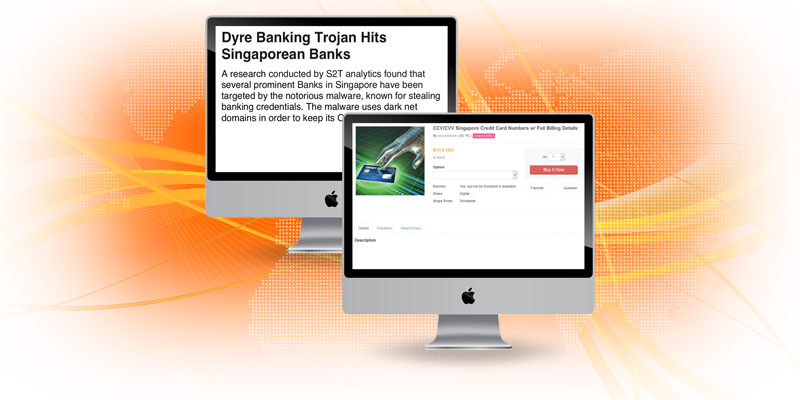

S2T Analytics offered tailored cyber threat intelligence subscriptions that provide organisations and cyber-security professionals with concrete and actionable information. We employ a pool of analysts with wide language skills, including Chinese, Russian, Spanish, Portuguese, Arabic, Farsi, Bahasa Indonesia, Urdu, Hindi, and Tagalog. This helps us provide comprehensive coverage of the threat landscape and address any threats specific to a particular organisation. Our team of intelligence analysts work closely with our cyber-security experts to ensure the intelligence produced is indeed actionable, for example by conducting malware analysis of new malware obtained by intelligence analysts.